This post will help you set up remote access to your Synology NAS server using Synology’s built-in QuickConnect and Dynamic DNS.
Both of these methods have pros and cons, and you’ll figure out which, when, and how to use each by the end of this page—that’s the idea anyway. Remember that you need to be pretty comfortable with networking to get this done right.
Feeling uninitiated? Check out the related posts in the box below first.

Synology NAS: What is remote access and why should I care
Remote access is an essential part of any server’s purpose. It happens all the time, and you might not be aware of it.
For example, when you access a website, you have a remote connection to the site’s web server—that’s so obvious that the “remote” notion is implied.
Or, when you backup your phone’s photos onto Google Photos, your phone has a remote connection to Google’s server.
Or, when you use your phone to check on a home network, home alarm, or surveillance system, a remote connection must have been established for that to work.
When you use a third-party service, like Google Photos, that connection is part of the service itself. But for a server you get for your home or office, you’ll need to set up that secure remote connection yourself.
And a Synology NAS server comes with lots of applications that can benefit from a remote connection. At the very least, you manage your server’s settings and other aspects when you’re on the go—just like the remote web management on a router.
So, in this particular case, you’ll learn here how to securely access data or services on a Synology NAS server located at your home or office when you’re out and about in the world.

Remote access on a Synology NAS server: QuickConnect vs. Dynamic DNS
On a Synology NAS server, you have two options for remote access. One is a vendor-assisted feature called QuickConnect, and the other is the generic Dynamic DNS.
Let’s start with QuickConnect.
QuickConnect: Quick doesn’t necessarily mean fast
QuickConnect is a built-in feature of all Synology NAS and routers. It allows you to use:
xyz.quickconnect.to
or
quickconnect.to/xyzas the address to access your device via the Internet, using a web browser.
In this case, xyz is a unique name called QuickConnect ID. It’s a string of Unicode characters.
So if you replace it with dongknowstech, you’ll get:
dongknowstech.quickconnect.to
or
quickconnect.to/dongknowstechas the address to access the server remotely. Specifically, opening that address on a browser will take you to the server’s web interface, similar to hitting its local IP address when you’re at home.
For the rest of this post, as a demo, I’ll use dongknowstech—you should use a QuickConnect ID of your own, one that has not already been taken. By the way, this address is not case-sensitive. So, “DongKnowsTech” works too.
QuickConnect’s quick facts
QuickConnect is available in all Synology NAS servers and Wi-Fi routers and is part of the Control Panel.
If you use DSM 7, it’s in the “External Access” section. On DSM 6 and older, QuickConnect is a section on the menu.
QuickConnect’s pros
- Built-in, easy to use
- Reliable and consistent
- No port-forwarding is needed on the router
QuickConnect’s cons
- Slow: All requests have to go through Synology first. As a result, it’s not ideal for data-intensive apps, such as Share Sync or Folder Sync.
- Privacy risks—an account with Synology is required and your server is attached to the vendor via this account.
In many ways, QuickConnect is an indirect, remote access solution that’s great for lightweight applications such as the server’s interface, DS Cam, DS Video, or Synology Photos.
Generally, if you don’t need more than 5MB/s—that’s 40Mbps—connection speed, QuickConnect will work well. Considering most broadband connection has relatively slow upload speed, QuickConnect will work well in most cases.
With that, let’s move to the steps on how to set up QuickConnect on your server.
Steps to setup QuickConnect on a Synology NAS server
These steps are done on the server’s web user interface. The steps below are for a server running DSM 7 with notes for those running DSM 6. The two versions of the OS are similar enough on this front.


- Open the interface and go to Control Panel.
- Go to External Access on the menu and then pick the QuickConnect tab. (On DSM 6, QuickConnect is a section of its own.)
- Check the box Enable QuickConnect and you’ll be prompted to sign in with a Synology account or the option to create one if you haven’t. Do so.
- Enter the QuickConnect ID (which is dongknowstech in this example) and click on Apply.
- Answer the prompt affirmatively. The system will take a few seconds to register the ID—assuming it’s not already taken.
- Click on the Advanced button to check/uncheck the services and applications that can be accessed via QuickConnect.
And that’s it! And you’re all set. Going forward, the QuickConnect ID is all you need to enter into a Synology app to access the service in question.


Dynamic DNS and Synology NAS server: More work, but you’re in control
The way Dynamic DNS works, you just need to set up a port forwarding entry for your server on your router.
Dynamic DNS’s quick facts
Dynamic DNS or DDNS is a generic remote access feature available in most home routers.
The feature turns the router into the DDNS device that binds a unique domain to the network’s WAN IP. A user then can use the domain to dial back home.
(A Synology NAS server can work as a DDNS device, too, but in this case, you’ll have to get a Synology account.)
Dynamic DNS’s pros
- Fast performance: The speed is limited only by the network’s broadband.
- Private: No user account with the hardware vendor is needed.
- Flexible: The user can customize the domain name, ports, etc.
Dynamic DNS’s cons
- The setup process can be involved
- Port-forwarding is needed for each client/service. One server might need more than one port-forwarding entry. (You don’t have the luxury of just checking the boxes as shown in step #6 of QuickConnect above.)
- Certain DDNS providers might require an annual fee
Dynamic DNS is independent of a particular device within a network so it’ll work with all of them. Most of the time, you just need to figure out the device’s open port or ports for certain services and configure the setting on the router.
Many routers, such as those from Asus, come with one DDNS domain for free.
For this post, I assumed that you have set up Dynamic DNS for your router’s WAN IP. If not, this post will explain DDNS in detail with steps on how to set one up.
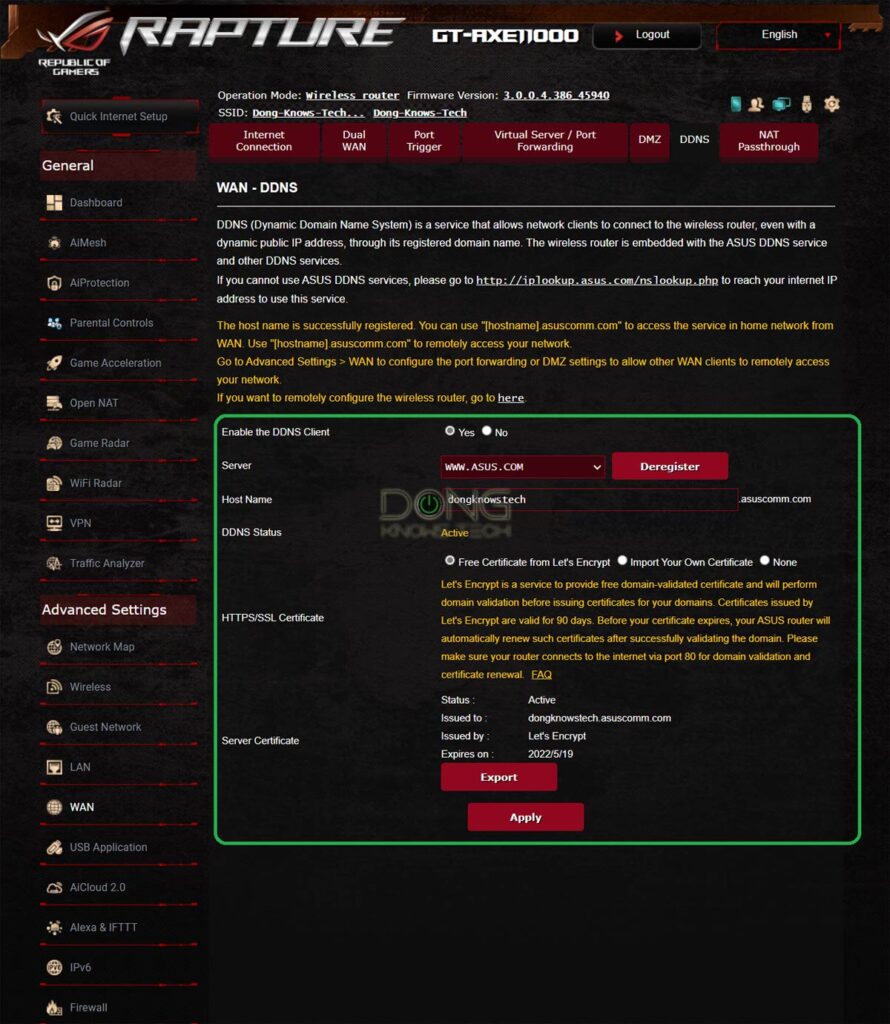
Also, I used an Asus GT-AXE11000 router and Asus’s free DDNS service with the following domain:
dongknowstech.asuscomm.comBut you can use any DDNS service and a domain of your own.
With that, let’s proceed on how to set up port-forwarding so that you can access your Synology NAS server’s web user interface over the Internet.
1. Figure out the port number and the IP address of the server
By default, the ports used for a Synology server’s user interface are 5000 for HTTP and 5001 for HTTPs.
Generally, you might want to change those to something else for security reasons. If you’re going to do that or trying to figure out the current port numbers being used on a particular Synology NAS server, here are the steps:


- Log into the server’s web user interface locally.
- Open Control Panel and then Login Portal and use the DSM tab. (If you use DSM 6 it’s Control Panel -> Network -> DSM Settings.)
- Change or note down the port numbers for the server’s login page.
For this post, though, we keep the default ports.
As for a server’s IP address, there are many ways to figure that out. You can do that via the router—below—or when you configure the server. If you need more, this post on IP address will help.
2. Add the port-forwarding entry for the port in question
You do this on your router.
Most home routers support port forwarding, and you can do this via the mobile app or the web user interface. I’m a fan of the latter.

As pictured here, port 5000 is forwarded to 192.168.88.108, which is the server’s local IP address.
By the way, you can use a new external port and keep the internal port the same, which would give the same effect as changing the port on the server and keeping the two the same.
The steps vary from one router to another, but the port-forwarding is generally in the WAN section of the router’s interface. Here are the detailed steps on an Asus router:
- Open the router’s web user interface.
- Open the WAN section on the mentu
- Navigate to the Virtual Server / Port Forwarding tab
- Click on Add profile and choose to forward port 5000 and 5001 to the server’s IP address. You can use a separate entry for each port as I did in thise case or use a port range (5000-5001).
And that’s it. From now on, you can access the server’s web interface from any internet-connected computer by going to the address(es) mentioned above.

You will need to repeat these for each service of the server. So, for example, the Synology Drive Share Sync uses port 6690, which requires another port-forward entry if you want to use the service via DDNS.
Change your mind? To remove an entry, click on its trash bin icon and the entry is no longer and the application will stop working remotely.
3. Accessing the server’s login page remotely
Once you’ve finished step #2, the server is now ready to be accessed from outside.
Per the rule of calling a port, and assuming the default ports are being used, here’s how to call access the interface of the NAS server I used in this post’s example.
From any Internet-connected computer outside of the network where the server is, open a web browser and point it to:
http://dongknowstech.asuscomm.com:5000
or
https://dongknowstech.asuscomm.com:5001And that’s it. You should be viewing the login page of the server itself.
Conclusion
There you go, now you can manage your Synology server remotely. As for Synology QuickConnect vs. Dynamic DNS, it’s a matter of convenience vs. control, speed, and privacy.
In any case, you can always use both—you’ll note how DDNS is much faster than QuickConnect. So use it for apps that involve moving a lot of data around.
Once you have figured things out, keep in mind that you should change the default port numbers for security purposes, at least on the WAN (external) side.
Indeed, while for this post, I kept the default ports numbers for demo purposes, changing the default port numbers and keeping the login account secret are good practices to keep your server safe from hackers. More on that matter, check out this post on Synology server’s security.






As an admin for a Synology NAS DS718+ running DSM 7.1-42661 update 2, I should be able to set up QuickConnect IDs for multiple users, right?
But when I try to set up more than one user (non-admins), QuickConnect assigns them the SAME connecting URL. Example:
1st user:
http://quickconnect.to/user1name
2nd user:
http://quickconnect.to/user1name
QuickConnect is at the server level, Selim, meaning it works for all user accounts. But each account, once successfully logged in, will have the access level (to shared folders and apps) set by the admin user. What you’re envisioning is irrelevant. The username you might see there is just saved there by the browser and has nothing to do with how QuickConnect works.
Hi,
Thanks for the clear instructions!
However, i seem to have a problem with the port forwarding, mainly because I have a TP link Mesh Wifi, I have done the port forwarding in my GNON modem, but cant seem to access my tplink settings.
Fair Noobie, any help is appreciated!
That’s because you have a double-NAT setup, V. More in this post.
@dauhee
Investigate using Cloudflare DDNS (free and easy interface) and setting up OpenVPN on the synology. Change the default port that is used for the OpenVPN connection. See if your router/firewall can do geoblocking and https/ssl inspection – this add some layers of protection. But as Dong said – if something is accessble from the internet it will never be 100% safe/secure.
Thanks for the input, Thom. I wanted to add, as you might have implied, that a VPN will make the remote connection more secure, but your server itself still faces the Internet the same. The server’s security should be handled by the user account, blocking, .etc, as I mentioned here. A VPN will not make the server, which hosts the VPN connection, any more secure, and the firewall will not do anything when you use DDNS or QuickConnect, as I did on my demo server used for this post. The idea is that you open a secure door to the server, so you should keep the lock of that door secure, not trying to hide the server itself which would defeat the purpose.
Hi Dong,
Would you have any thoughts on which option is more secure? DDNS doesn’t involve 3rd party which is appealing but then the NAS is sitting on the internet which is scary
Thanks
It seems the option you’re looking for is to stay off the Internet completely, Dauhee. DDNS has nothing to do with security — more in this post. And there’s no such thing as absolute security. Your server is already “sitting on the internet” as long as your network has Internet, hence always vulnerable — more in this post.